
Secure identification methods
PIN codes
Choose 6 or 8 digits rather than 4, and don’t use a sequence like 123456.
Fingerprint
An older technology, but still protects you from shoulder surfing.
Choose facial recognition
Even safer than fingerprint. The most advanced systems like Apple’s Face Id create a detailed 3D map of the user’s face.
Enable automatic screen lock
Locks your screen after a set time of inactivity, for example after a couple of minutes.
Software updates
Updating your OS (Operating Systems like Windows, iOS etc) is crucial for ensuring security.
Here’s why
It patches vulnerabilities that could be exploited by hackers, improves performance, fixes bugs, and adds new features.
Top tip
Turn on Automatic Updates on your phone and laptop – that way you won’t have to worry about this.

Apps
When downloading apps, remember this:
Official stores
If your IT policy allows app downloads, only download from reputable stores like Apple Appstore, Google Play, Microsoft Store etc. These stores have vetting processes to try and weed out malware.
Official apps
Make sure you download the official app – popular apps often have clones or apps with similar names and logos. They might not be malware, but will retrieve personal data from you.
Hardware accessories
Tip 1 – Reputable sources
Only use accessories provided by your IT department or purchased in reputable shops if your IT policy allows it. Choose well known brand names.
Tip 2 – Don’t use stuff you find
Do not use USB accessories or memory cards that you find in public spaces like hotel lobbies, airports etc.
Tip 3 – Other people’s accessories
Think twice before you let someone plug in their accessories to your devices, especially your work computer.

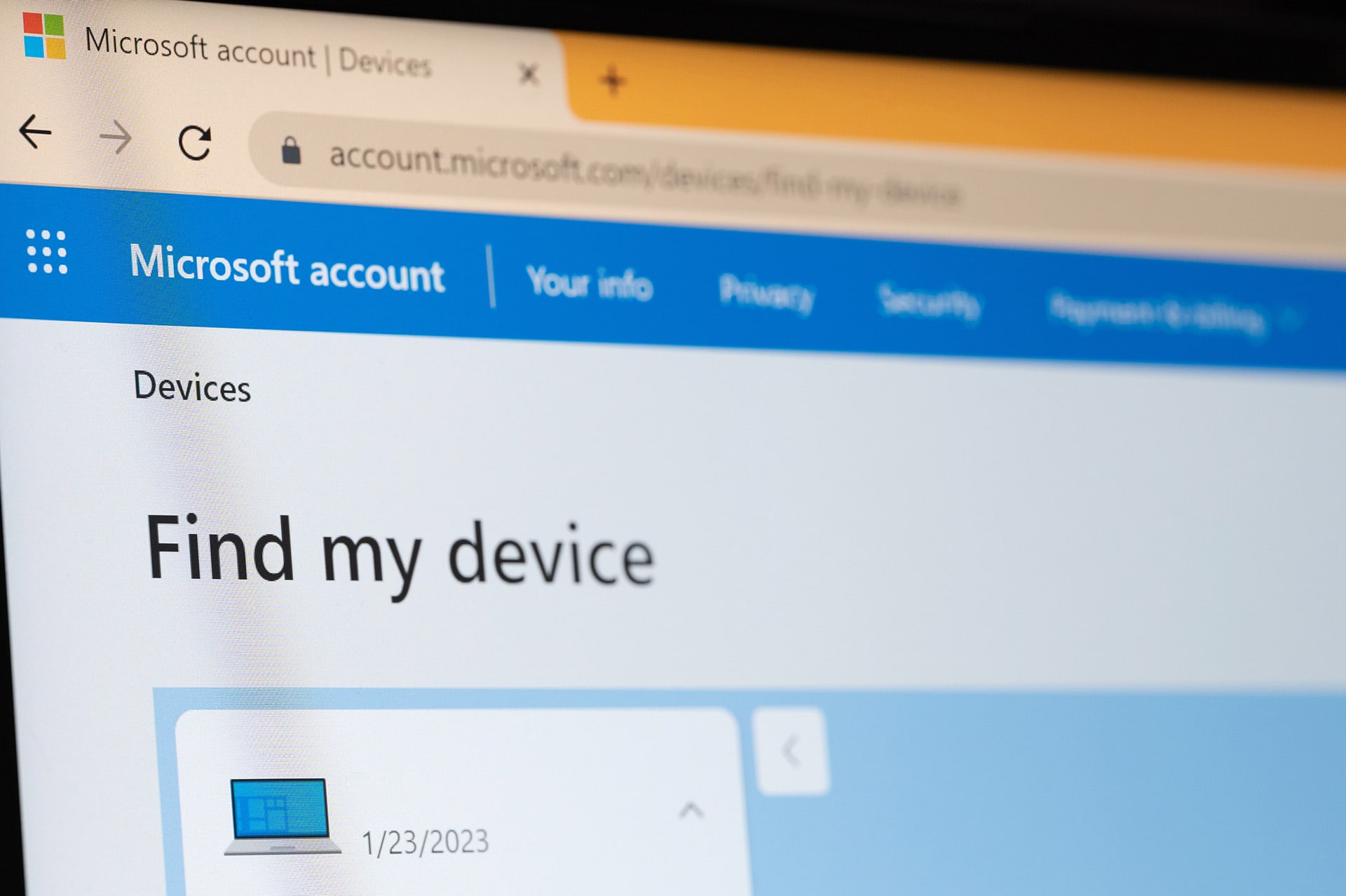
Loss or theft
What do you do if you lose your phone or computer? First, speak to IT and follow your guidelines.
If it is a personal device, you can log in to your Apple, Google or Microsoft account. If enabled, there is a feature called Find my device (or similar) that can help you.
For more details, visit these help pages by Apple, Google and Microsoft.
1. Find it
Step one is to locate your missing device. It may be visible on a map.
2. Lock it
If the device is not in your immediate vicinity, you can lock the device remotely. This way, you limit how it can be used.
3. Wipe it
Finally, if you don’t expect to retrieve it again, you also get the option to permanently delete all data on your device.

